Hi guys, its been a long time since I have posted something on this blog post. I was busy with a project which I would be sharing on this post. I will not be publishing any ctf soon, maybe later in the year or so.
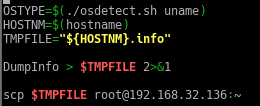
So, the reason I have not been publishing any CTF writeup, was because I was working on my first ever project, to develop an auditing script to automate the checklist from CIS Benchmark.
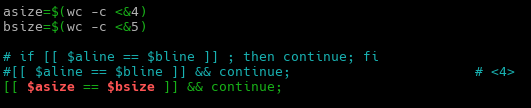
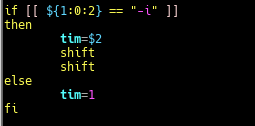
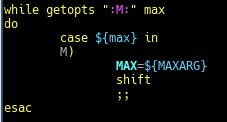
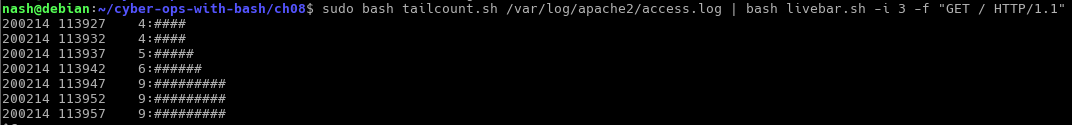
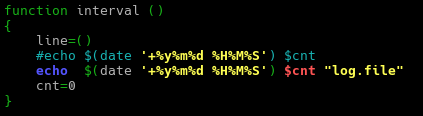
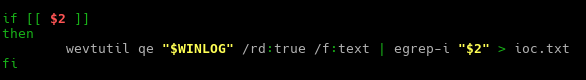
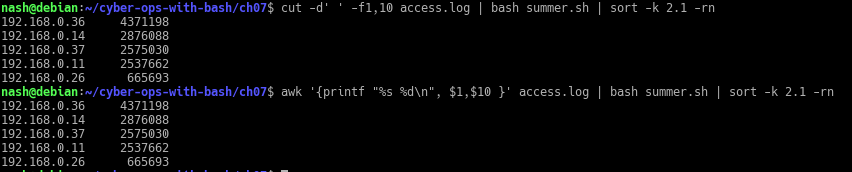
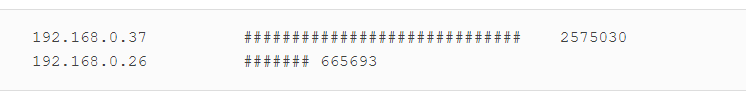
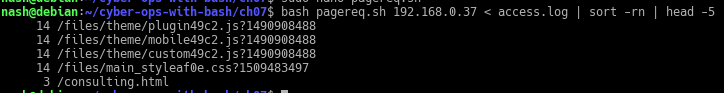
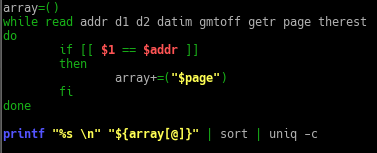
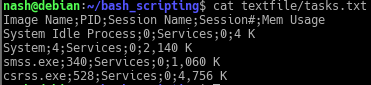
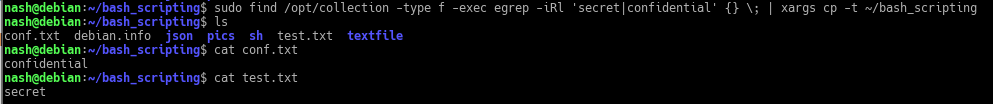
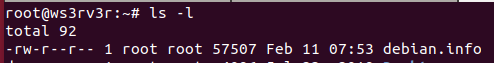
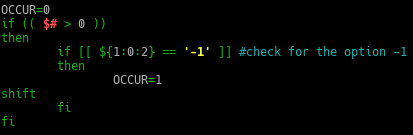
The audit script created was to audit CentOS 8, a linux based operating system. The script checks from the filesystem to the network, permissions of the files and users etc. It was quite interesting for me because I have to plan the flow of my scripts from top to bottom. Examples, like where do I append the results to? What are the variables needed and in which direction should the script executed?
All this planning and writing out a script/product really challenge myself, to use my understanding of Linux, bash and the solution provided from CIS-Benchmark, to piece it together to write out an auditing script.
At the end of 3 months plus of hard work and pulling my hair out because of bugs in the script. I was able to successfully finished it and published it on GitHub.

For me publishing something on github really gave me a sense of accomplishment. However, my belief is that the scripts I created is to be improve it to make it better for the community.
Thus writing this post, I would like my readers to visit my Github, and do a code review. I always believe that other people view of codes are different and in some ways help to improve ones coding skill when people share their opinion.
Hence, I would like my readers to provide me constructive criticism, give me feedback on what to improve or add on to the script. All views are welcome. I would really love the community to check it out. If the script is good, please do leave a star 🙂
The link to my Github is here.
And like how I always end my post, is to say “Thanks for reading and have a good day peeps.”
Author: Derek